Privileged Access Management as a Service
Empowering you to focus on your core business.
"Minimizing operational overhead through a flexible and cost-effective subscription-based solution while securing privileged access."
Struggling with complexity
THE COMPLEXITY OF DEPLOYMENT
PAM solutions often require significant time and resources for configuring hardware, installing software, and integrating with existing systems.
HIGH MAINTENANCE OVERHEAD
Maintaining on-premise and cloud PAM solutions can be resource-intensive and may require dedicated IT staff and infrastructure.
COST CONSIDERATIONS
On-premise PAM solutions often entail significant upfront costs for hardware, software licenses, and implementation services.
COMPLIANCE CHALLENGES
Ensuring compliance with industry-standard regulations may require additional resources and efforts leading to increased costs.
.jpg?width=500&height=308&name=Man%20glasses%20blue%20light%20Shutterstock%202023%20(large).jpg)
TOTAL COST OF OWNERSHIP
A combination of initial, operational, indirect, and hidden costs that accumulate during the lifecycle due to resources, technology, and knowledge:
- Hardware, software, and implementation
- Maintenance, support, training, and personnel
- Integrations, downtime, and compliance
- Scalability & opportunity costs
Reinforcing business resilience
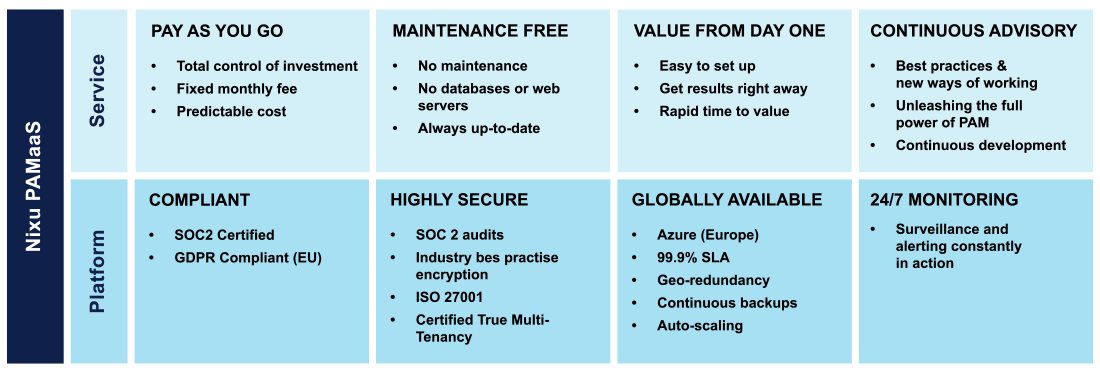
EFFORTLESS ONBOARDING
Ensuring efficient implementation without burdening IT operations while minimizing operational overhead.
- Swift integrations
- Rapid deployment
- Immediate value creation
STREAMLINED OPERATIONS
Highly compatible cloud solution ensuring operational excellence through high performance and availability.
- Extensible
- Easy to scale
- Maintenance free
COMPLIANT & SECURE
The continuous advisory service provides support and guidance throughout, helping to achieve improvements in:
- Industry-based regulations
- Security standards
- Future-proof decision-making
Creating value from day one
- Kimmo Hintsanen, Tech Lead
Stress-free turnkey service
RAPID DEPLOYMENT
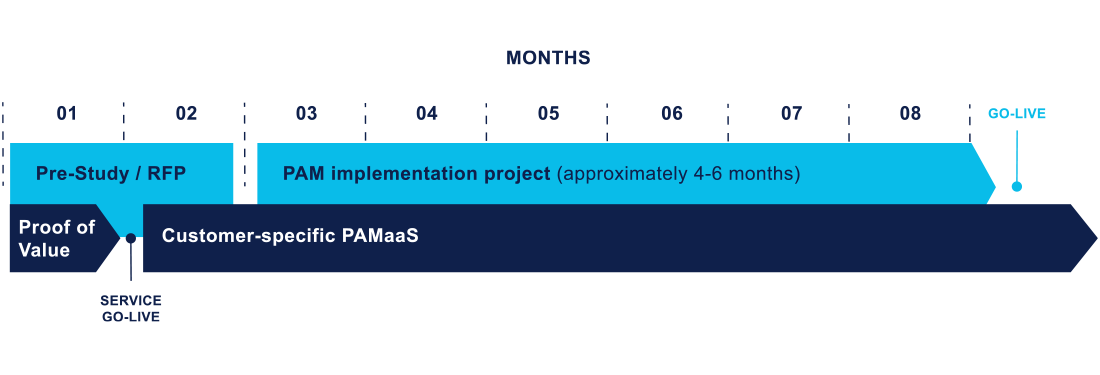
Proof of Value provides an alternative for a regular RFP enabling you to verify the value and decide on continuation within a month without commitment.
SCALABILITY
A scalable solution that can effortlessly adapt to the evolving needs of organizations without requiring additional infrastructure or resources.
REDUCED MAINTENANCE
All the maintenance responsibilities included to the service reducing the burden on internal IT teams and minimizing operational complexities.
CONTINUOUS ENHANCEMENTS
Security, compliance, threat mitigation, and service performance are always up to date without customer intervention.
COST-EFFECTIVENESS
No upfront or separate implementation costs. Fixed monthly fee guarantees the predictability of the cost structure.
CONTINUOUS ADVISORY
Certified experts provide continuous advisory, guidance, and support maximizing the value of the investment.
Accomplish more with less
REINFORCED BUSINESS RESILIENCE THROUGH PRIVILEGED ACCESS MANAGEMENT
This whitepaper is a key tool for businesses looking to enhance their cyber security and protect against emerging threats, focusing on how Privileged Access Management strengthens resilience by addressing and mitigating challenges.
After reading this whitepaper, you will be able to:
• Understand why privileged accounts require protection and their critical importance in cyber security.
• Recognize various types of privileged accounts and their significance in organizational security.
• Identify common challenges organizations face in managing privileged accounts.
©2025 Acme Co, Inc. All rights reserved. Privacy Policy
.jpg?width=2000&name=shutterstock_2140028027%20(2).jpg)
